Testing and rooting out bugs are integral parts of any successful application development process.
Most prominent software development standards, including the popular Agile method, include provisions for making sure the end-product operates according to the use cases that define the required functionality.
But by focusing solely on functional requirements, the organizations that use these methods fail to address non-functional issues, including application security testing.
Many argue that customers buy functionality as opposed to security, a mindset that justifies dealing with application security as an afterthought. However, when we consider the damage done by recent data breaches, we can see that security flaws have the potential to be much more destructive than functional glitches, yielding far deeper impact on customers and vendors alike. This warrants the need to integrate application security testing into the software development lifecycle (SDLC).
Although application security testing is finally beginning to draw the attention it deserves among some developers, it all too often leads to additional frustration, difficulties, and effort, which results in security moving down developers’ lists of priorities.
Some firms even avoid application security altogether for the sake of releasing a feature-complete product on time.
Contrary to popular belief, application security testing doesn’t need to be an arduous process. In this post, I’ll introduce five easy steps that will help you to integrate security testing into your software development lifecycle seamlessly and without incurring too much technical and managerial overhead.
Use Static Application Security Testing Tools
Static Application Security Testing (SAST) tools are a software development team’s best friend. As opposed to dynamic testing tools (DAST), which only work on compiled and executable binaries, SAST scans at the source code level, which makes it easier for individual members of a development team to apply.
Since developers engage in application security testing in the early stages of the development process, SAST helps cut the costs and rippling effects that are attributed to the late discovery and correction of security risks.
Moreover, for the most part, SAST application testing can be automated and transparently integrated into the development process, thus minimizing the extra effort that usually goes into assessing applications for security.
Checkmarx, for example, is a security tool that enables developers to self-test their code before committing it for compile, far before launch. Checkmarx actively helps in discovering security flaws on an SAST basis, and the solution also offers recommendations for fixing bugs and for complying with development best practices.
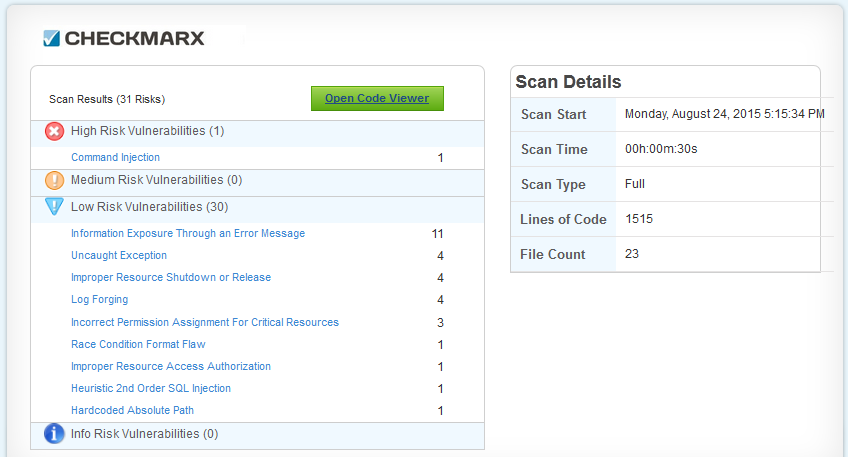
Because SAST helps development teams catch security vulnerabilities early on in the development lifecycle, developers, project managers and application security professionals can more easily make adjustments along the way, thus helping to safeguard agility.
Fit Security Testing Into Your Development Lifecycle
The key concept here is integration. AppSec and development professionals do not have to necessarily conflict with their responsibilities, and security testing should not be a separate phase of your development process.
Rather, you should incorporate security in parallel to all other development disciplines, including requirement analysis, software design and construction. Distributing application security testing into smaller tasks can make the job easier, faster and cheaper.
In addition, you will need to determine the priority of each task. By classifying them based on their nature and criticality, you’ll be able to schedule bundles of tasks for each iteration and make sure all of them get covered throughout the software development lifecycle.
For instance, making sure that user input is escaped to prevent SQL injection and Cross Site Scripting (XSS) attacks is a crucial task that needs to be performed at each iteration. Other tasks, such as user account control (UAC) testing are not as critical (albeit important) and can be scheduled to be carried out at every two or three iterations.
Perform Threat Modeling on New Features
Some security vulnerabilities result from coding bugs, such as using a function (sprintf is a good example) that is prone to buffer overflow attacks. Finding and fixing coding bugs like these, however, is the least of your problems.
The more challenging part of application security testing is finding vulnerabilities that stem from design flaws, such as bad sanitation techniques and weak encryption, which can turn into major headaches if you find out about them too late into the development cycle, when dozens or even hundreds of modules will break if you fix the bug.
In order to avoid such unpleasant surprises, every new feature introduced into the application should be examined from a security perspective, in order to determine if it can be exploited for malicious purposes.
Threat modeling involves examining your application and its code from a hacker’s perspective and looking for ways it can be compromised. Anticipating and planning for security implications in advance can spare you from a lot of trouble that comes with design flaws that lead to security loopholes. This way, you can identify and mitigate the threat before other layers of code settle on top of it and make it more challenging to fix.
Ensure Communication Among Security Team Members
Communication is the heart of teamwork. If you don’t facilitate communication between different teams involved with your application’s security testing process, there’s a good chance that individual members will get carried away with focusing only on their own concerns. Keep an open line of communication across management, the AppSec team, and the software developers, so that everyone is aligned regarding priorities, expectations and goals.
An automated solution such as Checkmarx helps streamline communication among different members of the development team, as the entire suite can be integrated into the tools used by the developers, such as IDEs, bug tracking tools, build servers, source code repositories and reporting systems.
Its dashboards and viewers provide your team with a centralized means to communicate and manage security alerts and flaws, as well as track enhancements and changes that your software undergoes throughout its lifecycle.
Employ Foundational Security Practices
In essence, application security testing should become an integral and essential part of your development process. You can make sure that every member of your development team becomes responsible for the security of the products you create, which contributes to the overall reliability of your product.
Developers are, by nature, focused on functionality, whilst AppSec professionals will focus on security. Internalizing security into your organization’s culture will require that developers are well aware of secure coding techniques and best practices.
Aside from just focusing on features, they will need to be aware of potential attack vectors, common security flaws in programming languages, and bad coding habits to avoid. Knowing what to do, and what not to do, helps a lot in plugging security gaps from the get go.
Also, adopt security testing standards and metrics for your applications. For instance, making sure that applications run with underprivileged accounts can prevent disasters even when security holes are discovered in your application.
A final foundational measure is to periodically review the architecture of your software from a security perspective. Stay focused on how systems interact, and watch out for how outside actors can exploit APIs and other factors that are beyond your system’s boundaries.
By having distinct measures of what secure application standards are, you are more likely to find and fix potential security flaws before your app goes into production. You can also check your coding style and structure against security standards defined by prominent institutes such as SANS and OWASP, as a matter of best practice.
Final Thoughts
Iterative processes such as the Agile method become much more powerful when you can ensure the security of your product. With the right practices and the right set of tools, you can make sure that you build secure apps in a frictionless way and eliminate unpleasant and expensive security surprises that may haunt your team after the release of your application.
