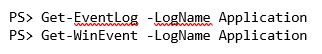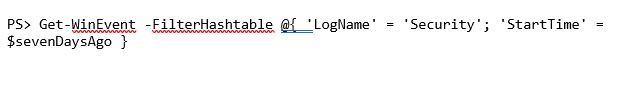The Windows event log is one of those ubiquitous products that nearly every Windows system administrator has experience with. When there is a break, unexpected change or security breach, the Windows event log is usually the first place to look.
When inspecting the event log via the event viewer, it's hard to narrow down what you're looking for if your search spans multiple event logs or if you need to search for events across many computers at once. In that case, PowerShell can come to the rescue.
PowerShell has two cmdlets to read the event log: Get-EventLog and Get-WinEvent. Each cmdlet performs the same task in a slightly different way. Let's perform some common tasks and see how their syntax compares.
Listing event logs
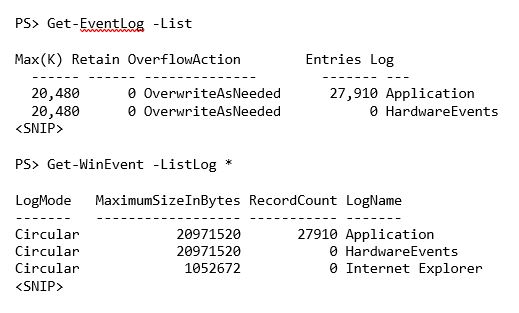
First, we can enumerate event logs. Using Get-EventLog, we can use the List parameter, while Get-WinEvent uses the ListLog parameter.
I cut off the output from both commands, but when you run both, you'll immediately notice that Get-WinEvent returns a lot more logs. This is because it's capable of querying the logs that show up under Applications and Services in the event viewer, while Get-EventLog cannot.
Querying individual event logs
Once we know the logs available to query, we can then narrow down the query to a particular event log using either cmdlet.
This will output each event in the event log you provide to the LogName parameter on either cmdlet in chronological order. But what if you need to find specific events? In that case, you'll need to filter.
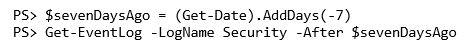
There are many different ways to filter events using both cmdlets, although more so with Get-WinEvent. For example, perhaps I want to see all events in my Application event log that happened a week ago or earlier. With Get-EventLog, after defining the date seven days ago, I can use the After parameter.
We can do something similar using Get-WinEvent, although this time, we have to use one of its filter parameters. In this instance, I'll use the FilterHashTable parameter.
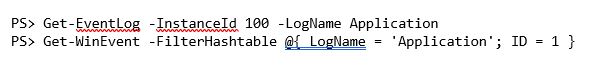
Maybe we'd like to find only those events that match a specific ID. Both cmdlets can do that too.
Get-WinEvent > Get-EventLog
There's a lot we can do with both cmdlets, but Get-WinEvent takes the cake in sheer functionality. Excluding the fact it can query many more types of event logs than Get-EventLog, its filtering ability can't be beat.
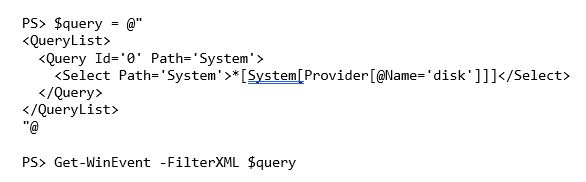
In the cases above, we were using the FilterHashTable parameter, but this is just one example. Get-WinEvent also supports filtering events by their native XML format using FilterXML. For example, if we would like to find all events with a provider name of "disk" in the system event log with an event ID of 1, we could define the XML as below and pass that value to the FilterXML parameter.
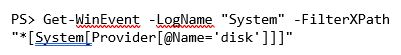
Is defining all of that XML not your thing? No problem. We can use XPath too.
Get-WinEvent provides many options to filter events, making it far superior to the Get-EventLog cmdlet in terms of functionality.
Summary
We just scratched the surface as to what these two cmdlets can do. In a nutshell, if you need to perform simple event log queries, Get-EventLog is probably going to be easier to work with. If you find yourself needing to create complex queries across local and remote computers, Get-WinEvent is a much better choice.